Imagine having the power to uncover vulnerabilities in a digital fortress before the dark forces of the cyberworld exploit them. Welcome to the first episode in our series on penetration testing insights.
I can promise you that after completing this series, you will become familiar with the basics of penetration testing with regard to ethical practices.

This series is suitable for those who might be considering penetration testing as a career or deciding on a cybersecurity degree. So after finishing this series you would decide whether this would be your career of desire or not. It’s also a useful refresher for anyone preparing for an interview, including myself.
Let’s begin by defining penetration testing – we’re the heroes seeking vulnerabilities in a website and securing them before the ‘bad guys’ can exploit them.
Let’s simplify it; imagine we’re playing the role of Mr Harry Potter, and our mission is to find the “Horcruxes” (vulnerabilities) before Lord Voldemort threatens our nice and safe magical world.

Moving away from fiction, we are going to follow professional standards for conducting penetration testing, usually conducted in five stages. In this episode, we will begin with the first stage, which is Engagement.
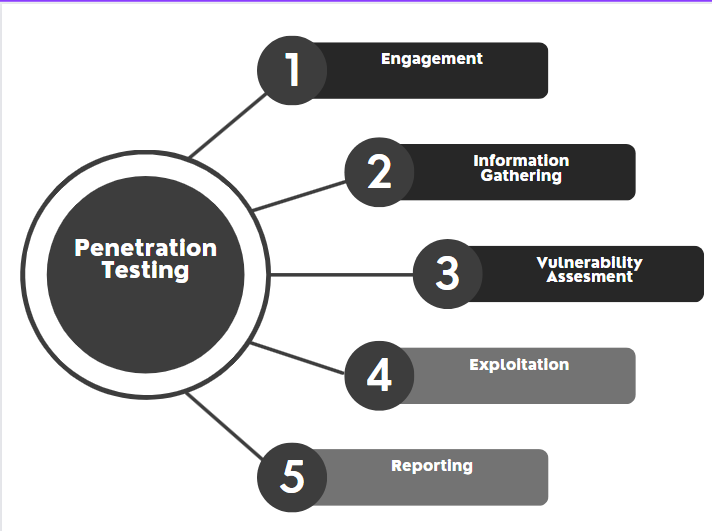
Understanding Engagement is crucial, especially if you are going to work for a company that provides penetration testing services to various clients, or if you are going to work as a freelancer.
The reason is that this stage provides the means of ethical hacking. It emphasises the legal aspects and what you are allowed to do. For example, you will need to agree with the client on which specific ports you are allowed to test, the nature of the testing, and whether the testing is only related to scanning vulnerabilities (Stage 3) or can extend to exploitation (Stage 4) as well. This would also be important to agree on because it will outline the possibility of any of their services going down due to any heavy scans performed.
Let’s jump back to fiction so imagine that you are Mr Harry Potter again, and 10 years after graduating from Hogwarts (the client) is asking you to go in a hunting mission, your old friend Mrs Granger wants to accompany you, so do you think she will let you go to the mission without having a clear roadmap.

So our roadmap will be the Marauders map which will include the spells (tools and methods), and which areas of the castle (the client system) you are alowed to wander around without needing to wear an invisibility cloak.
That’s enough for this episode. In the next episode, we will start playing with Kali Linux – let the games begin!
Before I let you go, I would advise you to watch this guy’s video if you don’t already have Kali Linux installed. This guy did a good job showing how to install it in a virtual box.